Although User Environment Management (UEM) becomes more and more important in almost every company it is getting easier to convince the IT people and management of purchasing the UEM. However there are still people who just see such a product as a logon script replacement, which can also be done using scripting or Group Policy Preferences. I’m not writing this article to discuss or argue about that statement as you can do actually a lot of the same configuration with scripts or Group Policy Preferences for the basic set-up like printer assignment, network mappings and so on. However UEM products offer much more other functionalities like Profile Management, E-mail management, Trouble Shooting tools, Performance Management and additional Security Management. This last one can be a real important added value for lot of companies, but is often not taken into account by the decision to use/purchase a UEM product. In this article I will focus on the security part showing/describing the features available in RES Workspace Manager 2012 (most of those features are also available in other UEM products as well) and provide you with use cases where those features were implemented and created an added value for that company.
Managed Applications
In almost every User Environment product it is possible to configure authorization on executables, arranging that users can only start the applications/executables they are assigned to. I know with the Group Policy Management there is a similar feature. However I have never seen an implementation of this in production, because of the complexity and limitations this option within Microsoft has. UEM products are going into much more details and are easier to manage and maintain. With RES Workspace Manager (RES WM) this is part of Managed Applications. Within RES WM you can create applications and assign those shortcuts to the user via several methods. Those pre-defined applications are automatically allowed to start by those assigned users. For other applications or executable(s) used by those applications as an administrator you can allow those executables. You can allow them on the application (shortcut) level or on a global level. It’s preferable that you use the application level as much as possible; I only allow default Windows executables on the global level.
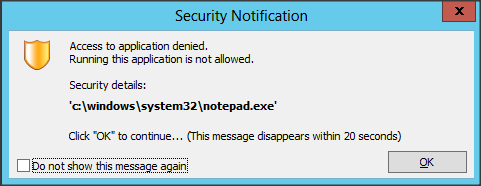
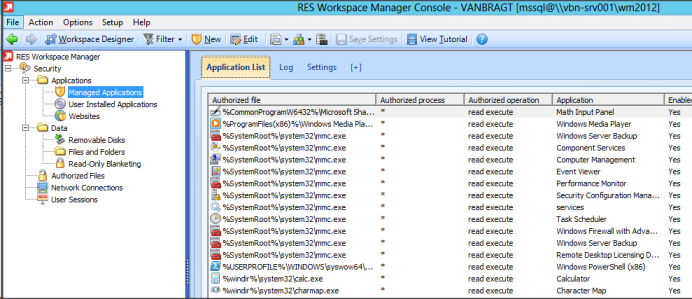
Every executable which is not allowed for the end-user will be blocked (when Managed Appliation is enabled). The end-user will be provided with an (adjustable) error message (currently only one message can be defined, which is difficult in a Multilanguage organization) and within the console a mention in the log will be made. Out of that log the application can be authorized if necessary.
Almost all my customers using RES WM are using this feature. Mostly to arrange that users can not start “dangerous” executables which can damage the XenApp environment or can cause performance degrees. Also some customers are using it to arrange that users can only start the application which they bought a license for that specific user(group). Remember that UEM product is not automatically accepted by all vendors as a probate solution for license management.
User Installed Applications
With RES WM you can assign specific rights to (a group of) users, so they can install applications on the workstation on their own (without intervention of IT and without local administrator rights). With the integration of RES WM the IT department knows which applications are installed by which (authorized) user on which system, manage the placement of the shortcut and arrange that the application is automatically added to the Managed Application Security. The IT department has the option to allow any installation by that user(group) or use whitelisting or blacklisting to define which installations are (not) allowed.
Personally I did not use this option at any of my customers, because the needs or requirements were not there. This feature however is discussed on a regularly basis this year, so there is definitely a good use case for controlled User Based Application installation. I can think off use cases at hospitals, research departments and legal departments.
Websites
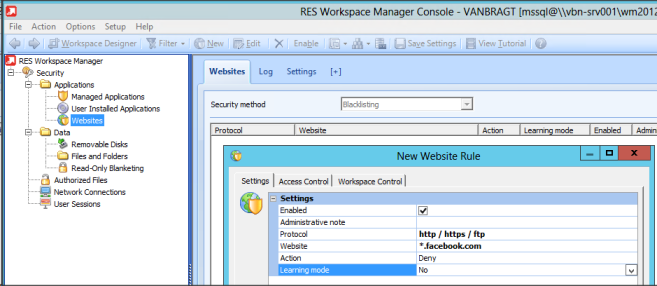
Another security component within RES WM is Websites. With this feature regulation of accessing websites (both internal as external) can be arranged. Again you can use whitelisting or blacklisting. Just as the other component a log is created in which websites are mentioned which were tried to open by user(s) which were not authorized. Out of this log you can add those websites when required.
While almost all companies have a fully operational proxy server which can arrange the same functionality it depends if you can find a use case for this functionality. For companies without a proxy infrastructure this option can be very useful to regulate the internet traffic (for example using blacklisting to prohibit specific websites). Also it can be used for securing internal websites for access to a specific group (as the webhosting product does not support this possibility).
Data Access
RES WM can also arrange that users can (or can’t) use specific data. This can be done on three levels:
- Removable Drivers
With this option you can regulate the usage of Removable Drives on workstation. A removable drive can be a floppy drive, cd/dvd drive and/or external harddisks/memory sticks. Different kind of access can be arranged to those devices: no acces, read, modify or a combination. So you can configure that a user can write to a CD/DVD device, but cannot read it (or can read a cd/dvd, but not write data on it).
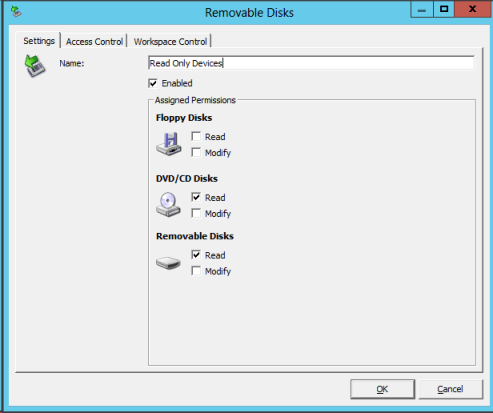
This option is used a lot at my customers using workstations mostly used to remove one of possibilities to get data out of the company by any user. Also customers are using it to provide access to memory stick for a specific group of users. Also one customer is using it in learning mode. Learning mode arranges that actions on removable disks are logged, but not prohibited. They can use the log afterwards to see which data is copied on/from the network by which user.
- Files and Folders
With Files and Folders specific folders or files can be authorized or prohibited. This feature is mostly used to prohibit running specific content like videos or music files. For example you can prohibit access to MP3 or VOB files for all or a specific user group. You can also think of specific script files like VBS.
This feature is also used at several customers for prohibiting the execution of content, although with all media content it’s getting more difficult to block all kind of multimedia files. However there are still valid worker groups like manufacturing personal, doorkeepers and gateman’s.
- Read Only Blanketing
With Read Only Blanketing you can configure the local hard disks in a read only mode. In theory things sounds like a perfect solution, while users can’t write anything to the local disk (except the configured exceptions like the user profile) the system (XenApp/RDS server) can’t get compromised and users cannot save their document by accident locally (and don’t lose the data because they can’t find it anymore afterwards). Out of practical experiences I must admit that it is pretty difficult to enable this feature without disturbing the user experiences. Many applications are writing temporary files on the local disk using the user context. So the list of exceptions can be pretty large and difficult to maintain.
At Several customers where we enabled this feature to arrange that users don’t lose date, because they have written it the local disk by accident. Many of them decided to disable the feature, mainly because the exceptions were not manageable or applications are using too many random place and random file to, causing messages at the end-user side too often.
Network Connections
The last option I would like to mention in detail according to arranging security is network connections. With this option you can set-up a layer 7 based (application) firewall. You can specify (again in whitelisting of blacklisting mode) which IP (ranges) on which port(s) can or cannot be accessed. Just like wit all other features can filter the rule with several control (access control, location/devices and workspace control), which makes it very flexible.
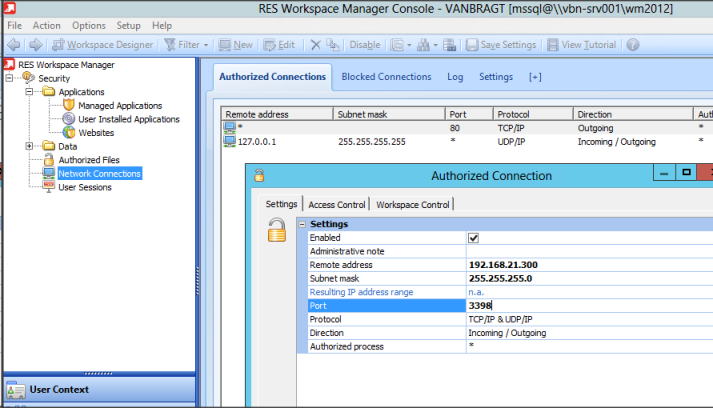
This option is very useful when access to systems should be limited to specific user groups without using separate VLANs and Firewalls at Layer 3 level. At one customer this arranged that instead of using silo’s for each specific access rights (via Firewall Layer 3) we can offer one central desktop where all users are connecting and RES WM arranges that users can access only the system they are authorized for. Check the customer case Everything on Top where I describe this use case a bit more in detail.
Conclusion
With this article I tried to show you that User Environment Management products offer also additional functionality that is not offered in the default Microsoft Tools or at least arranges that the implementation is much easier and better to manage. It depends per customer/use case if those security options are offering an added value. Also those Security options are not the only functionality that offers added value of UEM products that should be taken into account when discussing User Environment Manager products like RES Workspace Manager.
